Six Reasons People Laugh About Your Convert To Ico
페이지 정보
작성자 Jerrell 작성일25-02-14 09:45 조회6회 댓글0건본문
주소 :
희망 시공일 :
It may be seen as the time required for a deobfuscator to cut back the potency of the obfuscated program, i.e. the time needed to make it extra readable by a human. Thus, the worldwide quality of an obfuscation can be seen as a function of the potency (complicated a human), resilience (confusing a deobfuscator), and the overhead it introduces (execution time and size of the information). It should not be mistaken with minification which is solely the very fact to decrease the size of a file. Although minification makes the file unreadable, it’s extremly easy to present it a traditional look, and then to understand or modify the code at ease. By offering an API that makes distant calls to the server containing the important logic, the consumer has no longer entry to the code. On the flip side, probably the most premium company plan prices $54/month, which helps you to monitor 75,000 backlinks a month, observe 2500 key phrases each day, ship 2500 API requests a day, and search 2500 keywords. The starter plan of Zutrix starts at $9/month, which includes 10,000 backlink monitoring credit, 250 keyword tracking credits/daily, 250 API requests, and 50 key phrase searches. Zutrix uses the latest AI applied sciences to provide you with the most correct rank-monitoring results each single time.
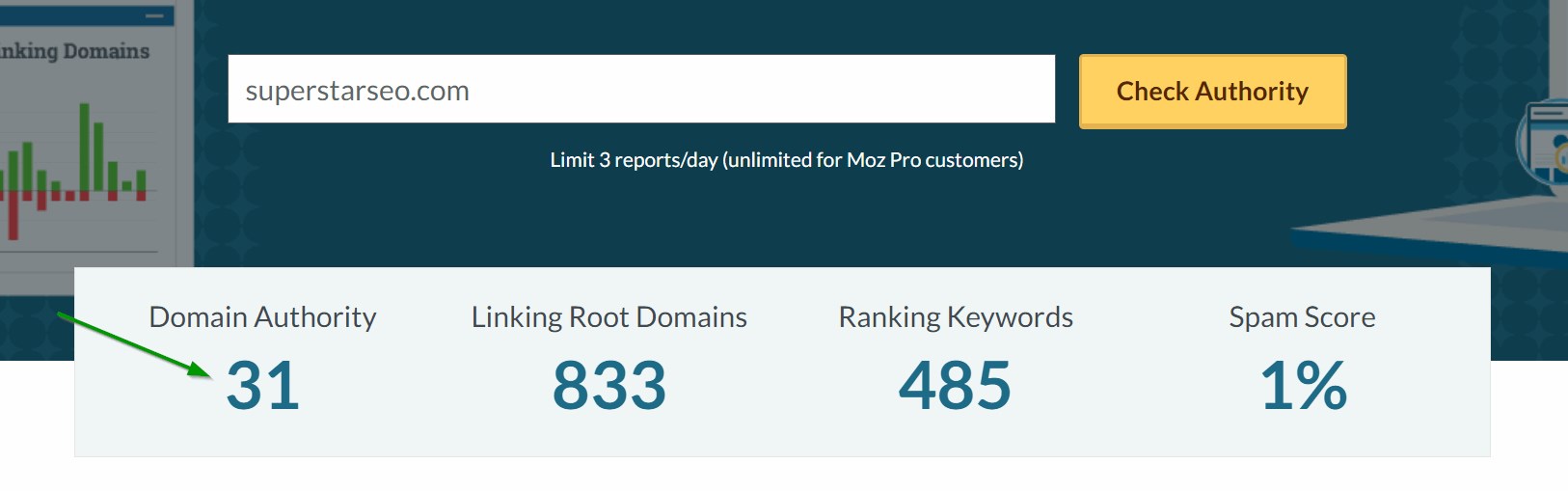 Nov 29, 2014Backup Status in 'Site Backups''Site Backups' now shows the standing of the newest backups (successful or failed). 2019s domain on a scale from 1 to 100. The higher the score, the more doubtless the site will rank well in search engine results. You can simply find out all of the flaws and increase your site area moz authority check upfront. To extend the area authority of an internet site, first, you? Review the new fees in detail and update your listings to optimize their visibility and appeal, and probably improve your income. Early termination fees will not apply to DSL service terminated within the thirty (30) day cash-back assure period. By using a Linkbuilding service resembling FatJoe, you sit again and so they get the hyperlinks for you. Get spam scores of every backlink and simply disavow the spammy hyperlinks right out of your dashboard. Kwebby permits customers to set the variety of backlinks proven by their free backlink checker, which might be set to a minimal of 10 and a maximum of 100. Naturally, we gravitated toward testing the tool to its utmost potential. 102. What is the distinction between compatibility testing and configuration testing? If all these important functionalities are working wonderful, you'll be able to transfer forward with installing extra software and conducting additional testing.
Nov 29, 2014Backup Status in 'Site Backups''Site Backups' now shows the standing of the newest backups (successful or failed). 2019s domain on a scale from 1 to 100. The higher the score, the more doubtless the site will rank well in search engine results. You can simply find out all of the flaws and increase your site area moz authority check upfront. To extend the area authority of an internet site, first, you? Review the new fees in detail and update your listings to optimize their visibility and appeal, and probably improve your income. Early termination fees will not apply to DSL service terminated within the thirty (30) day cash-back assure period. By using a Linkbuilding service resembling FatJoe, you sit again and so they get the hyperlinks for you. Get spam scores of every backlink and simply disavow the spammy hyperlinks right out of your dashboard. Kwebby permits customers to set the variety of backlinks proven by their free backlink checker, which might be set to a minimal of 10 and a maximum of 100. Naturally, we gravitated toward testing the tool to its utmost potential. 102. What is the distinction between compatibility testing and configuration testing? If all these important functionalities are working wonderful, you'll be able to transfer forward with installing extra software and conducting additional testing.

More formally, obfuscation may be defined as the process of transforming a program P right into a program P’ comparable to P and P’ have the same observable behavior. By obfuscating your program, you make it more durable for someone to know its behavior. The notion of observable conduct is necessary. 2. Click the "Convert to ICO" button to start out the conversion. Typically, you can wonderful-tune conversion parameters using "Advanced Settings" (non-obligatory, search for the icon). This data can assist you construct your 2020 content technique - aiming for incremental improvements to all of your metrics over time. Besides enabling the out-of-course of mode, it’s vital to feed raw information slightly than pre-parsed documents in, otherwise the harmful a part of the method occurs within the host application after all. Effectively attain out to site owners: It’s crucial to achieve out to the appropriate individuals at the correct time when asking for a hyperlink. So let’s get proper into it! Let’s verify whether we are right with our assumption.
댓글목록
등록된 댓글이 없습니다.